Blogs By this
author
- Comunet Case Study: South Australian Environment Protection Authority (EPA)
- Comunet Case Study: AWS Workspaces and Landing Zone for AFSS
- Comunet Acheives ISO 27001 Certification
- Comunet Case Study: AWS Cloud Migration for DIT
- Comunet Case Study: TRUMPS Migration for DIT
- Embracing the Modern Workplace
- Unlock Business Agility with Outsourced IT Services
- Social Engineering Attacks: Proofpoint’s 2022 Social Engineering Report
- Increasing Email Security to Avoid Business Email Compromise
- How to Protect Yourself Against Ransomware Attacks
- Cyber Security Risk Management – Threats are Evolving Much Faster Than Australian Businesses
- How to Avoid Being Scammed Online
- How to Prevent Phishing Attacks
- AWS Migration Competency – recognition of Comunet’s leadership and expertise in cloud migration services
- The Log4j Vulnerability: What Happened and What’s the Impact
- The Software Development Life Cycle
- What is a Business Analyst and what do they do?
- Christmas Cyber Security Tips
- Off the Shelf vs Custom Software – 7 Things to Consider
- The COVID-19 digital vaccination certificate and the value of cyber security audits
- Comunet and AWS – delivering secure, scalable and trustworthy services non-profits
Related blogs
to this blog
- Comunet Case Study: South Australian Environment Protection Authority (EPA)
- Comunet Case Study: AWS Workspaces and Landing Zone for AFSS
- Comunet Case Study: Kid Sense Child Development
- Comunet Acheives ISO 27001 Certification
- Comunet Case Study: AWS Cloud Migration for DIT
- Comunet Case Study: TRUMPS Migration for DIT
- What is ISO 27001 Certification?
- Protect Your Business: The Essential Eight and Beyond
- Embracing the Modern Workplace
- An Overview of ISO 27001:2022
- Social Engineering Attacks: Proofpoint’s 2022 Social Engineering Report
- Increasing Email Security to Avoid Business Email Compromise
- How to Protect Yourself Against Ransomware Attacks
- Cyber Security Risk Management – Threats are Evolving Much Faster Than Australian Businesses
- How to Avoid Being Scammed Online
- How to Prevent Phishing Attacks
- AWS Migration Competency – recognition of Comunet’s leadership and expertise in cloud migration services
- The Log4j Vulnerability: What Happened and What’s the Impact
- Christmas Cyber Security Tips
- The Value of Data
- The COVID-19 digital vaccination certificate and the value of cyber security audits
- Comunet and AWS – delivering secure, scalable and trustworthy services non-profits
- Passwords are not enough – why you need Multi Factor Authentication
- Building innovation culture
- Getting out of the swamp: Accelerated Data Lake on AWS
Why do On-Premises and Hybrid solutions present a higher IT security risk?
It’s based on IT security being primarily grouped into two factors - physical and virtual security.
In all environments except Public Cloud, both physical and virtual security must be understood, architected, and maintained by IT staff. IT team profiles are regularly profiled as being time poor, challenged by budgets and not able to keep up with the training required to stay ahead of the curve on all elements of IT.
By moving to Public Cloud, organisations can outsource the physical security elements, while maintaining responsibility and control of their virtual IT security architecture include policies, data protection, user access, networks and their software.
Yes, you would hand over physical security, but you are almost certainly doing this to an organisation better equipped to manage these environments.
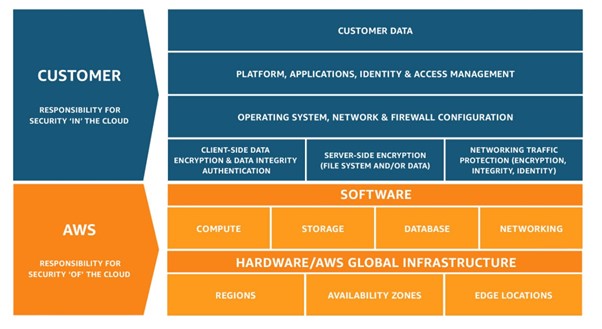
This is represented by AWS in their ‘Shared Responsibility Model’ where they define their responsibility as “Security of the Cloud”, with organisations only need to focus on “Security in the Cloud” – which is the same virtual security practises they need to have in on-premise environments today.
The Scout Motto – “Be Prepared”.
In summary, it’s important to remember that your workloads are not secure by default, in cloud or on-premises. Your team (or IT partners) must understand the shared responsibility models with each Cloud provider.
By leveraging the tried, tested and certified physical security of Public Cloud providers – you will not only have an environment which is ‘as secure’ as your own, but will find that you can surpass anything you can achieve in-house.
If you’d like to have a conversation around cloud security or any other IT risk related items – feel free to get in touch.